Cyber Security Headlines: Barracuda backdoors, undocumented iPhone hardware, NYT sues OpenAI December 28, 2023 Threat actors install backdoor on Barracuda appliances The company revealed that Chinese-linked threat actors exploited a zero-day vulnerability in its Email Security Gateway appliances. This resulted in deployed backdoors on a “limited number” of devices. The attacks used a code execution […]
Cyber Security Headlines: First American cyberattack, Iran APT campaign, ransomware victims spike December 26, 2023 First American suffers cyberattack California-based First American, which provides title insurance and settlement services for real estate companies and mortgage providers, confirmed the cyberattack on Thursday. As of this recording its website remains inaccessible, and the company is using a […]
FBI disrupts BlackCat, International operation nabs thousands, Sony data leak December 24, 2023 FBI disrupts BlackCat ransomware network On Tuesday, the US Justice Department announced that it has seized websites of the second most prolific ransomware-as-a-service operation, BlackCat, also called ALPHV or Noberus. The DoJ said the FBI has provided a decryptor to dozens of […]
HCL investigates ransomware, Agent Tesla returns, JavaScript bank malware December 22, 2023 Indian tech company HCL investigating ransomware attack The attack was reported to regulators on Wednesday and is being described as occurring in “an isolated cloud environment for one of its projects.” HCL Technologies is one of the largest tech companies in the world. […]
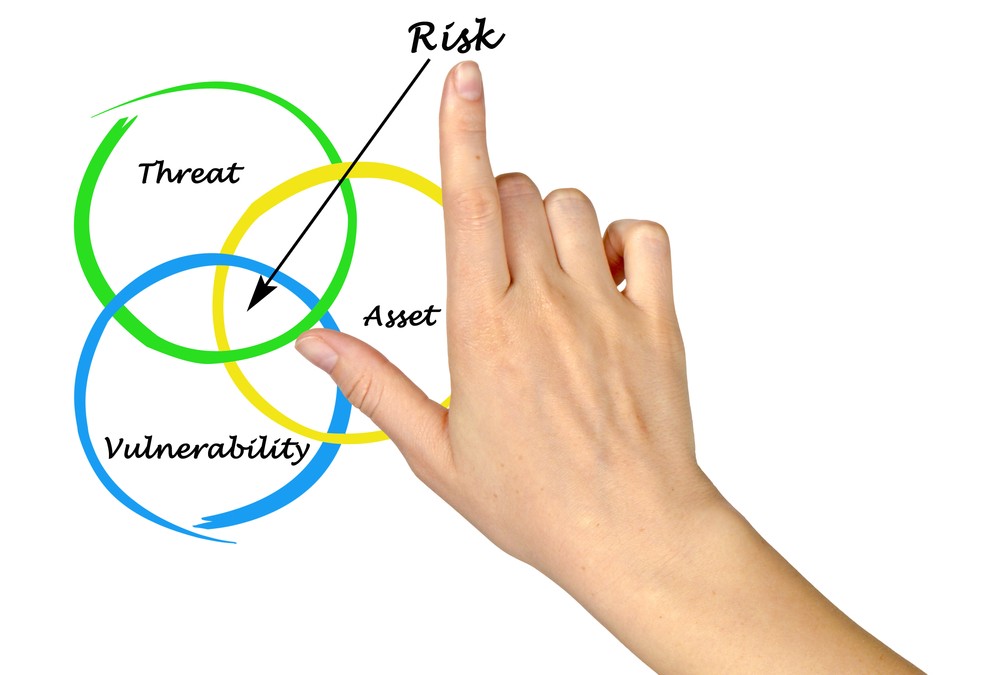
Introduction Vulnerability management is the process of identifying, evaluating, treating, and reporting potential risk areas identified within a system or software. Modern software can be very complex. Interactions with different applications, operating systems, and firmware often leave small gaps through which hackers can access and exploit a system. In this reading, you’ll discover some of […]
Principle of least privilege Security controls are essential to keeping sensitive data private and safe. One of the most common controls is the principle of least privilege, also referred to as PoLP or least privilege. The principle of least privilege is a security concept in which a user is only granted the minimum level of […]
In computer architecture, the server is an essential component of the client-server model. A server will provide a service for a client. Typically, one computer called the server will be reserved entirely for the execution of a given task. Then, additional computers are connected to this server, which awaits a request for a service. Much […]
Trojan Attacks The most frequent attack indicated in the chart is a Trojan attack. The name is a historical reference to the battle of Troy, when the Greeks were said to sidestep the defenses of the Trojans by tricking them into wheeling a wooden horse full of enemy soldiers into their own city. This […]
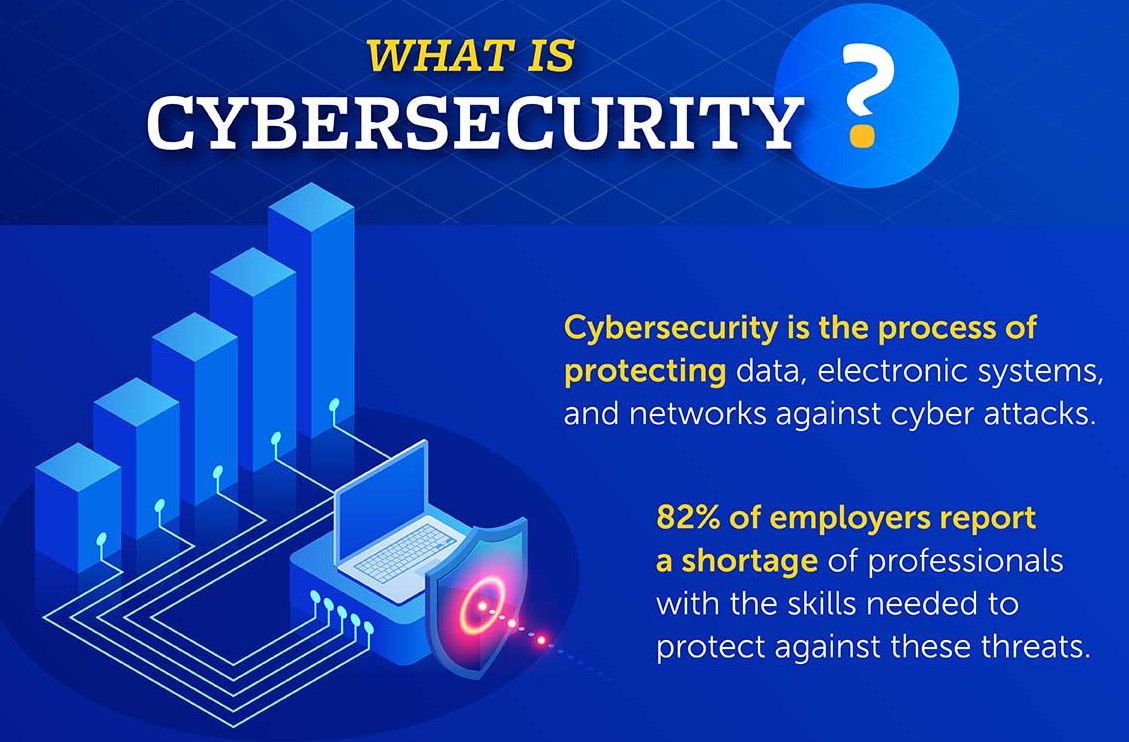
Cybersecurity is a set of processes, best practices, and technology solutions that help protect your critical systems and network from digital attacks. As data has proliferated and more people work and connect from anywhere, bad actors have responded by developing sophisticated methods for gaining access to your resources and stealing data, sabotaging your business, or […]
Previously, you were introduced to several technical skills that security analysts need to develop. You were also introduced to some tools entry-level security analysts may have in their toolkit. In this reading, you’ll learn more about how technical skills and tools help security analysts mitigate risks. An entry-level analyst’s toolkit Every organization may provide a […]