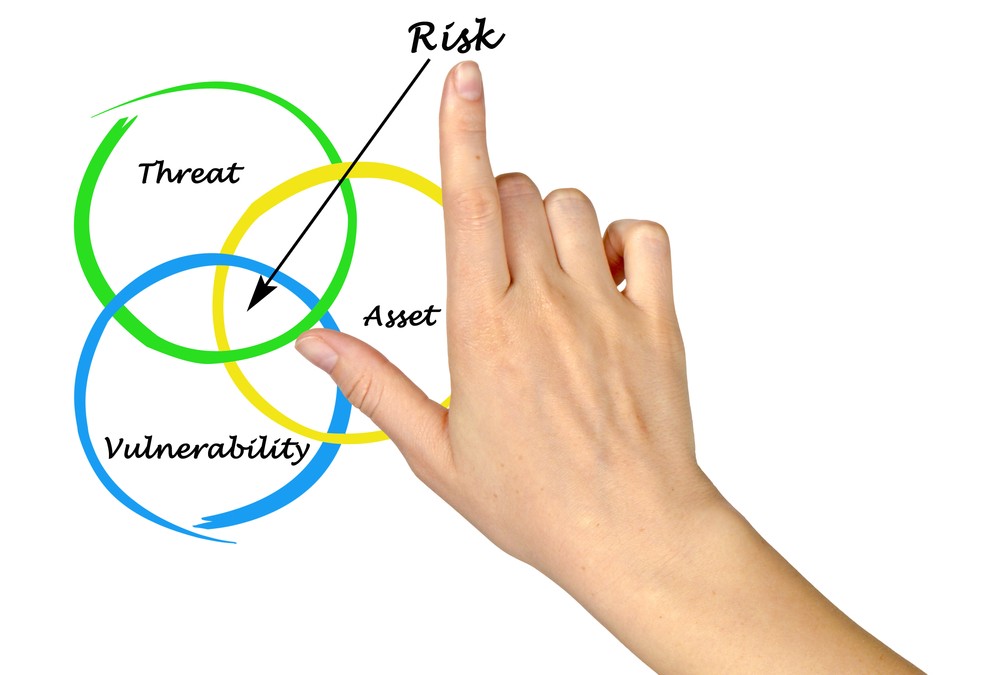
Principle of least privilege Security controls are essential to keeping sensitive data private and safe. One of the most common controls is the principle of least privilege, also referred to as PoLP or least privilege. The principle of least privilege is a security concept in which a user is only granted the minimum level of […]
In computer architecture, the server is an essential component of the client-server model. A server will provide a service for a client. Typically, one computer called the server will be reserved entirely for the execution of a given task. Then, additional computers are connected to this server, which awaits a request for a service. Much […]
Trojan Attacks The most frequent attack indicated in the chart is a Trojan attack. The name is a historical reference to the battle of Troy, when the Greeks were said to sidestep the defenses of the Trojans by tricking them into wheeling a wooden horse full of enemy soldiers into their own city. This […]
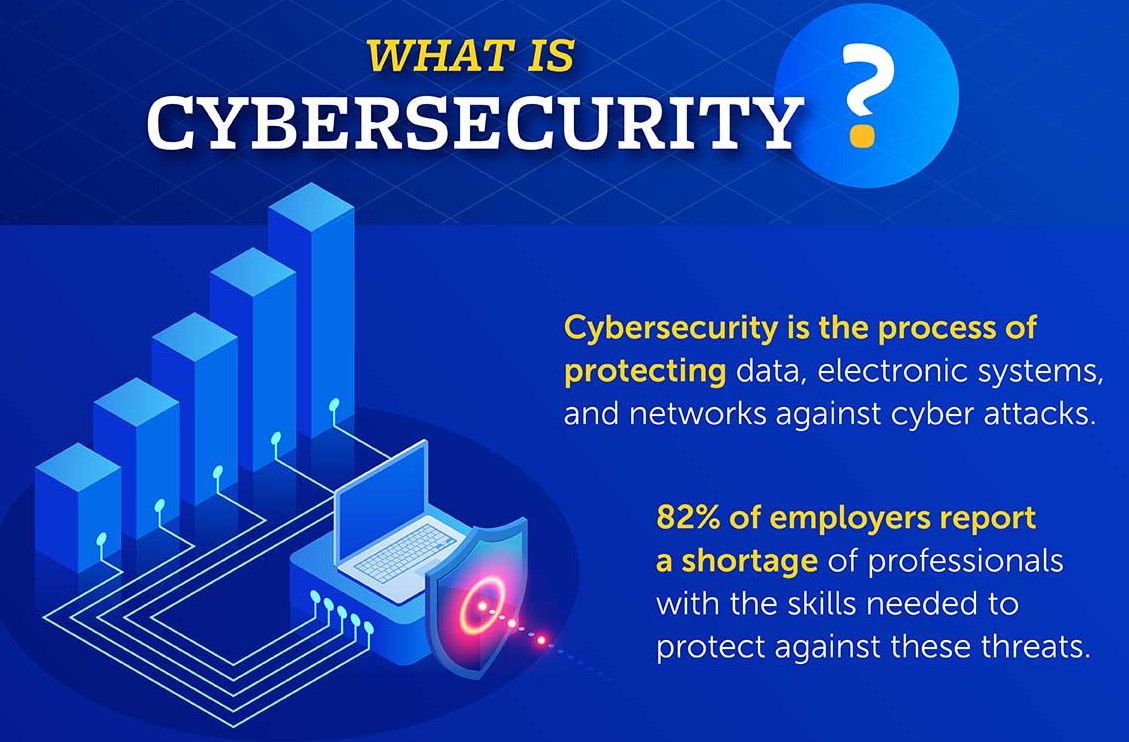
Cybersecurity is a set of processes, best practices, and technology solutions that help protect your critical systems and network from digital attacks. As data has proliferated and more people work and connect from anywhere, bad actors have responded by developing sophisticated methods for gaining access to your resources and stealing data, sabotaging your business, or […]